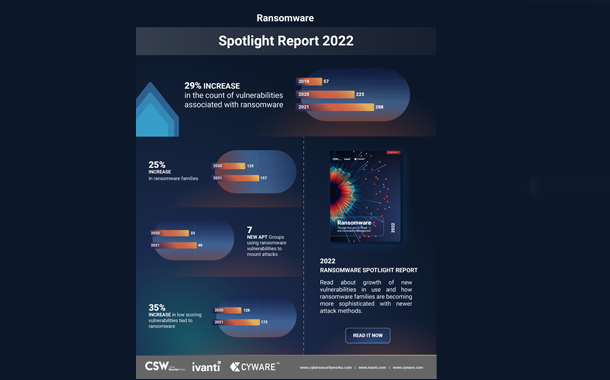
Ivanti, the provider of the Ivanti Neurons automation platform that discovers, manages, secures, and services IT assets from cloud to edge, announced the results of the Ransomware Spotlight Year End Report that it conducted with Cyber Security Works, a Certifying Numbering Authority (CNA), and Cyware, the leading provider of Cyber Fusion, next-generation SOAR and threat intelligence solutions. The report identified 32 new ransomware families in 2021, bringing the total to 157 and representing a 26% increase over the previous year.
The report also found that these ransomware groups are continuing to target unpatched vulnerabilities and weaponize zero-day vulnerabilities in record time to instigate crippling attacks. At the same time, they are broadening their attack spheres and finding newer ways to compromise organizational networks and fearlessly trigger high-impact assaults.
Below are a few top observations and trends from the Ransomware Spotlight Year End Report:
- Unpatched vulnerabilities remain the most prominent attack vectors exploited by ransomware groups. The analysis uncovered 65 new vulnerabilities tied to ransomware last year, representing a 29% growth compared to the previous year and bringing the total number of vulnerabilities associated with ransomware to 288. Alarmingly, over one-third (37%) of these newly added vulnerabilities were actively trending on the dark web and repeatedly exploited. Parallelly, 56% of the 223 older vulnerabilities identified prior to 2021 continued to be actively exploited by ransomware groups. This proves that organizations need to prioritize and patch the weaponized vulnerabilities that ransomware groups are targeting – whether they are newly identified vulnerabilities or older vulnerabilities.
- Ransomware groups continue to find and leverage zero-day vulnerabilities, even before the CVEs are added to the National Vulnerability Database and patches are released. The QNAP (CVE-2021-28799), Sonic Wall (CVE-2021-20016), Kaseya (CVE-2021-30116), and most recently Apache Log4j (CVE-2021-44228) vulnerabilities were exploited even before they made it to the National Vulnerability Database (NVD). This dangerous trend highlights the need for agility from vendors in disclosing vulnerabilities and releasing patches based on priority. It also highlights the need for organizations to look beyond the NVD and keep an eye out for vulnerability trends, exploitation instances, vendor advisories, and alerts from security agencies while prioritizing the vulnerabilities to patch.
- Ransomware groups are increasingly targeting supply chain networks to inflict major damage and cause widespread chaos. A single supply chain compromise can open multiple avenues for threat actors to hijack complete system distributions across hundreds of victim networks. Last year, threat actors compromised supply chain networks via third-party applications, vendor-specific products, and open-source libraries. For example, the REvil group went after CVE-2021-30116 in the Kaseya VSA remote management service, launching a malicious update package that compromised all customers using onsite and remote versions of the VSA platform.
- Ransomware groups are increasingly sharing their services with others, much like legitimate SaaS offerings. Ransomware-as-a-service is a business model in which ransomware developers offer their services, variants, kits, or code to other malicious actors in return for payment. Exploit-as-a-service solutions allow threat actors to rent zero-day exploits from developers. Additionally, dropper-as-a-service allows newbie threat actors to distribute malware through programs that, when run, can execute a malicious payload onto a victim’s computer. And trojan-as-a-service, also called malware-as-a-service, enables anyone with an internet connection to obtain and deploy customized malware in the cloud, with zero installation.