IDC InfoBrief “The Voice of the Analysts: Improving Security Operations Center Processes Through Adapted Technologies”. The security analysts are becoming less productive due to widespread “alert fatigue” resulting in ignored alerts, increased stress, and fear of missing incidents. To improve job satisfaction and effectiveness, the report also uncovered the top activities analysts felt would be best to automate to better secure their Security Operations Centers (SOCs).
“Security analysts are being overwhelmed by a flood of false positive alerts from disparate solutions while growing increasingly concerned they may miss a true threat,” said Chris Triolo, Vice President of Customer Success at FireEye. “To solve these challenges, analysts are asking for advanced automation tools, like Extended Detection and Response, which can help reduce the fear of missing incidents while strengthening their SOC’s cybersecurity posture.”
Security analysts continue to feel the pressure of increased alerts, spending almost half their time on false positives.
- False positives create “alert fatigue:” While analysts and IT security managers receive thousands of alerts every day, respondents indicated 45 percent of the alerts are false positives, making in-house analysts’ jobs less efficient and slowing workflow processes. To manage alert overload in the SOC, 35 percent of this group said that they ignore alerts.
- MSSPs spend even more time sifting through false positives, and they ignore more alerts: MSSP analysts indicated that fifty-three percent of the alerts they receive are false positives. Meanwhile, 44 percent of analysts at managed service providers said they ignore alerts when their queue gets too full, which could lead to a breach involving multiple clients.
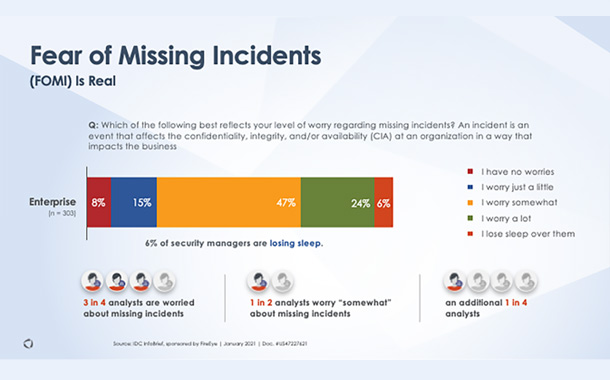
Fear of missing incidents (FOMI) is impacting a majority of security analysts and managers.
- As analysts experience more challenges managing alerts manually, their worry of missing an incident also increases: Three in four analysts are worried about missing incidents, and one in four worry “a lot” about missing incidents.
- Yet, this FOMI is plaguing security managers even more than their analysts: More than 6 percent of security managers reported losing sleep due to fear of missing incidents.
Analysts need automated SOC solutions to combat FOMI.
- Less than half of enterprise security teams are currently using tools to automate SOC activities: Respondents shared the top tools they use to investigate alerts, showing that less than half use artificial intelligence and machine learning technologies (43 percent), Security Orchestration Automation and Response (SOAR) tools (46 percent), Security Information and Event Management (SIEM) software (45 percent), Threat Hunting (45 percent), and other security functions. In addition, only two in five analysts use artificial intelligence and machine learning technologies alongside other tools.
- To manage their SOCs, security teams need advanced automated solutions to reduce alert fatigue and improve success by focusing on more high-skilled tasks like threat hunting and cyber investigations: When ranking the activities that are best to automate, threat detection was the highest (18 percent) on the analysts’ wish list, followed threat intelligence (13 percent) and incident triage (9 percent).