The DNS , a key component of the Internet infrastructure
In today’s world, the Internet is critical to both economy and society.The infrastructure is highly distributed amongst a wide range of players , such as ISPs, Internet exchange points & network access points, Telecoms carriers, Hosting providers and Registrars. They all play an essential role in how the Internet operates, and each is faced with a specific range of threats.
What is DNS ?
Humans can’t think like computers. they just can’t remember dozens of IP addresses. They need easy-to-remember names to locate their Mail server or their favorite Web pages. To make our lives on the Internet easier, DNS was therefore invented. It translates Host’s name into its IP address
How does DNS work?
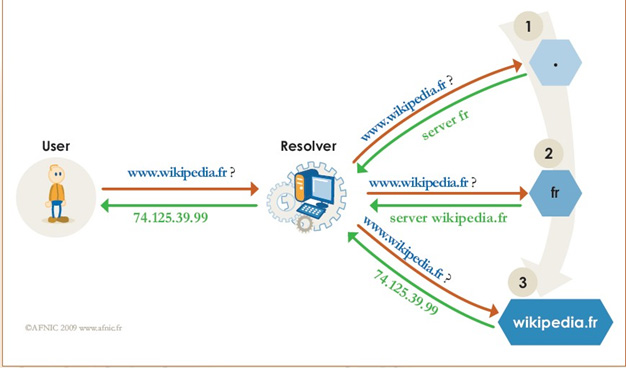
Internet is an IP network. Every host contains an IP address that must be known to any other host willing to communicate.DNS provides a way to know the IP address of any host on the Internet.
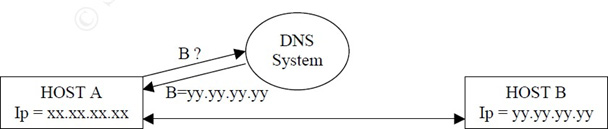
DNS is also a hierarchical service. Indeed a name has a structure: it can be server1.web.yahoo.com
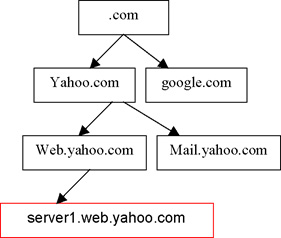
A host is a leaf on this tree, and any other node is called a “domain”. In our example, server1 is one of the hosts in the “web.yahoo.com” domain.
DNS continues to be a nice target for hackers
Purpose of DNS makes it a very sensitive area; for this is the place the client connection is orientated. The possibilities a black-hat can have by succeeding in hacking DNS are tremendous (a user can be directed to a host controlled by a hacker, whatever service he might be using: http, ftp, telnet … ).
There are two ways DNS can be hacked: by using protocol attacks (attacks based on how DNS is actually working) or by using server attacks (attacks based on the bugs or flaws of the programs or machines running DNS services).
Major types of attack targeting the DNS
DNS cache poisoning dupes the resolver into believing that the “pirate” server is an authoritative server in place of the original server. These attacks capture and divert queries to another website without any knowledge to users, the danger being that users might divulge personal data on what they believe to be a bonafide site.
DNS spoofing is a term referring to the action of answering a DNS request that was intended for another server (a “real” DNS server). This can be in a server- server exchange (a DNS server asks another for a mapping) or in a client-server dialog (when a client asks a DNS server for a mapping). There is no functional difference. The hacker “spoofs” the DNS server’s answer by answering with the DNS server’s IP address in the packets’ source-address field.
But this is not enough to spoof a DNS reply. DNS uses ID number to identify queries and answer, so the hacker needs to find the ID the client is waiting for. For that, he will use DNS ID hacking. With DNS spoofing, the hacker will try to impersonate the DNS reply so that the requesting client is misdirected, but without touching the DNS cache of the impersonated DNS.
Denial of service (DoS) attacks are attempts to make a given service impossible or very hard to access. Attacks sometimes use brute force (saturating servers by flooding them with simultaneous queries) or go for a more subtle approach by exhausting a rare resource on the server.
Distributed denial of service (DDoS) attacks are an elaborate form of DoS that involve thousands of computers generally as part of a botnet or robot network: a network of zombie computers that the attacker commandeers from their unwitting owners by spreading malware from one machine to another.
Reflected attacks send thousands of requests with the victim’s name as the source address. When recipients answer, all replies converge on the official sender, whose infrastructures are then affected.
Fast flux: In addition to falsifying their IP address, attackers can hide their identity by using this technique, which relies on fast-changing location- related information to conceal where the attack is coming from. Variants exist, such as single flux (constantly changing the address of the web server) and double flux (constantly changing the address of the web server and the names of the DNS servers).
How to protect
Each entity on the Internet is a link in the value chain, where all links are interdependent.
Hence , this advice is not aimed at a specific category of users, but to all those involved in the operation of the DNS: Top-level domain managers (registry), registrars, businesses, ISPs and so on.
Set up the best possible redundancy so that a server affected by an attack can be seamlessly replaced by other servers containing the same information, but connected to other networks. That is why registries such as AFNIC always require each domain name to be installed on no fewer than two name servers. Other more sophisticated techniques take redundancy to even higher levels with clear improvements in terms of security and performance.
Use the latest DNS software versions, especially BIND, and install the appropriate patches to prevent attacks exploiting well-known security loopholes.
Regularly keep an eye on the servers and their configuration, preferably from several points across the Internet. Due to the robust nature of the DNS system, it often happens that a server failure is only detected when the last server in the line also fails. To check the configuration, freeware is available, such as ZoneCheck.
Look into deploying DNSSEC, a DNS security protocol based on server authentication that reduces the threat of DNS cache poisoning.
Define a “business continuity plan” allowing the victim of an attack to continue or restore business with minimal downtime in the event of a major attack.
Conclusion
The security of the Internet infrastructure is based on roles being evenly distributed between different players (Service operators, ISPs, Registries, Registrars, Hosting providers, Internet exchange points, CERTs…). The wide range of structures, technologies and approaches represents one of the main guarantees for the Internet’s resilience.
Every player in this ecosystem must apply basic rules of the game for effective security: Coordination, Communication and Cooperation (the three Cs). In the case of the Internet, the variety and number of players involved raises a major challenge on both National and International level.
Given the changing nature and growing scale of threats, isolated or uncoordinated responses are likely to be increasingly ineffective. In a similar vein, continuing to raise awareness on security issues among the different players is one of the underlying actions.

