The month of February is always when people think of new ways to celebrate their love for their partners. It is also when cyber-criminals, as previously reported, think of new and creative ways to target and lure new victims with malicious activity. Especially during the current global restrictions enforced by the pandemic, which has driven significant increases in online shopping.
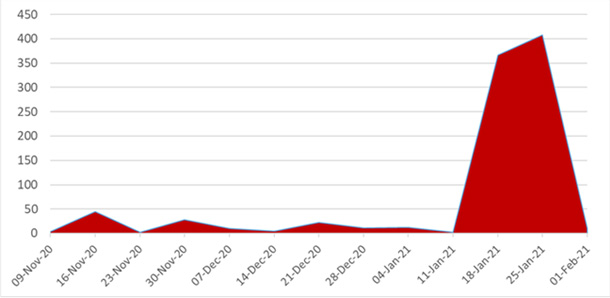
As people go online to purchase gifts for their loved ones during this period, Check Point Research (CPR) has observed a surge in malicious phishing email campaigns in the second half of January with over 400 malicious Valentine’s day themed individual phishing emails weekly.
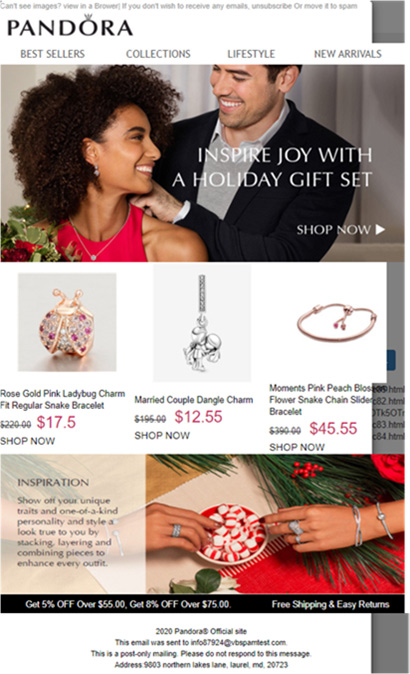
A real-life phishing email example: a Pandora lookalike campaign
Most of the phishing scams are focused on buyer fraud, and in some cases have reused themes and webpages from past phishing campaigns. For example, we found an email pretending to be from Pandora that was similar to one that we saw being used in Black Friday related campaigns in November 2020. The email’s aim was, as usual, to entice the user into purchasing jewelry items by offering them at unreasonably cheap prices, on a fake Pandora webpage which tries to imitate the look and feel of the real site.
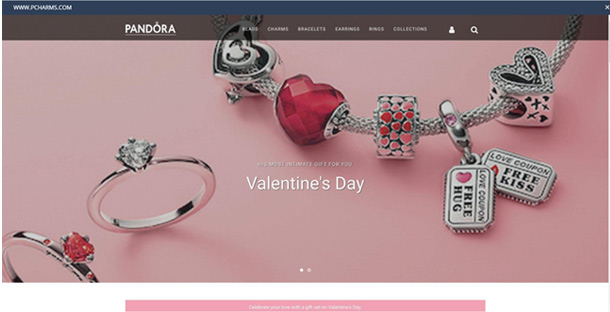
In the following example, you will notice that in the fraudulent email the year has not changed (“2020 Pandora Official site” instead of 2021) and the company address is written in lower-case (“northern lakes lane, laurel, md, 20723”). These are signs that the email is from a dubious source, and the website is fake. Of course, the sender name has been changed to imitate the brand, but the email address is clearly not related to it. Anyone who clicks on the links in the email will be redirected to a fraudulent page (www[.]pcharms[.]com) which tries to imitate the “Pandora” website.
From: Pandora Outlet (xwxrp@langqicyu[.]wang)
Email Subject: Valentine’s Day Give The Gift They Really Want…
Phishing website:
Why phishing attacks are so dangerous
Today’s phishing attacks can be extremely targeted. They are usually well planned , and backed by a huge amount of research. To ensure they are successful, attackers spend a lot of time studying their prey. Phishing attacks leverage different attack vectors, but the most common one is email. Other common attack vectors are phishing sites and text messages usually aimed at stealing credentials to perform account takeovers. These can lead to devastating results such as data loss, fraudulent money transfers and more. As mentioned, since these attacks are specifically designed to exploit the human nature of wanting a good deal, it is extremely important to prevent these attacks from ever reaching their desired victims – because even the most vigilant and cyber-savvy amongst us can sometimes get fooled.
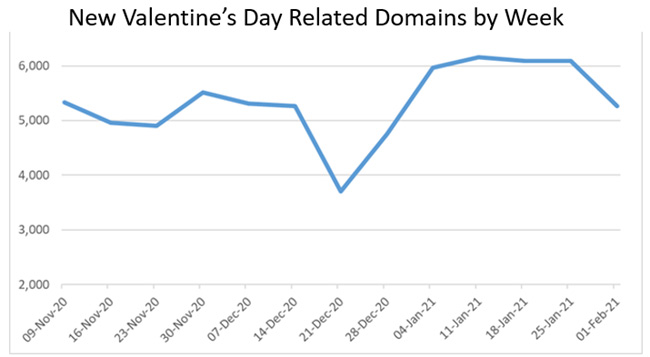
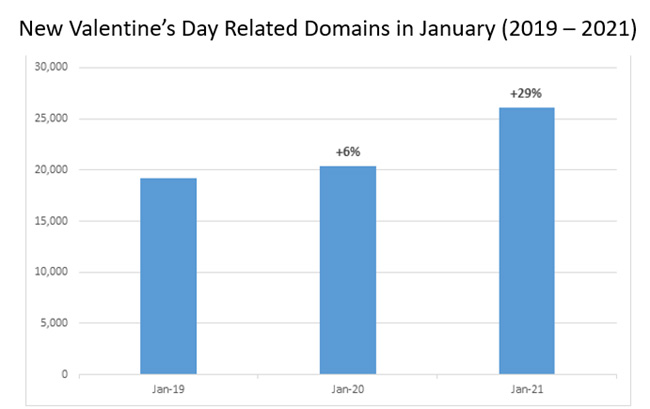
Spike in Valentine’s Day themed domains
In addition, throughout January CPR has observed a spike in the number of new Valentine’s Day themed domains registered. Out of the 23,000 new domains, 0.5% (115) were found to be malicious, and 1.8% (414) found to be suspicious. In general, there was a 29% increase in such domains registered in January, in time for the Valentine’s Day season.
How do you avoid falling victim to these fraud attempts? Here is what we recommend for a safer online experience:
- Verify you are ordering online from an authentic source. One way to do this is NOT to click on promotional links in emails, and instead Google your desired retailer and click the link from the Google results page.
- Never share your credentials. Credential theft is a common goal of cyberattacks. Many people reuse the same usernames and passwords across many different accounts, so stealing the credentials for a single account is likely to give an attacker access to a number of the user’s online accounts. Never share your account credentials and don’t re-use passwords.
- Always be suspicious of password reset emails. If you receive an unsolicited password reset email, always visit the website directly (don’t click on embedded links) and change your password to something different on that site (and any other sites with the same password). By clicking on a link, you can reset the password to that account to something new. Not knowing your password is, of course, also the problem that cybercriminals face when trying to gain access to your online accounts. By sending a fake password reset email that directs you to a lookalike phishing site, they can convince you to type in your account credentials and send those to them.
- Always note the language in the email. Social engineering techniques are designed to take advantage of human nature. This includes the fact that people are more likely to make mistakes when they’re in a hurry and are inclined to follow the orders of people in positions of authority. Phishing attacks commonly use these techniques to convince their targets to ignore their potential suspicions about an email and click on a link or open an attachment.
- Beware of “special” offers. An 80% discount on a new iPhone or an item of jewelry is usually not a reliable or trustworthy purchase opportunity.
- Beware of lookalike domains, spelling errors in emails or websites, and unfamiliar email senders.
Check Point’s anti-phishing solutions include different products that address different attack vectors – email, mobile, endpoint and network
The statistics and data used in this report present data detected by Check Point’s Threat Prevention technologies, stored and analyzed in ThreatCloud. ThreatCloud provides real-time threat intelligence derived from hundreds of millions of sensors worldwide, over networks, endpoints and mobiles. The intelligence is enriched with AI-based engines and exclusive research data from the Check Point Research – The intelligence & Research Arm of Check Point.

