Preface
Zero trust security is a new buzz word in the cyber space. Initially the model for The Zero Trust Network, or Zero Trust Architecture, was crafted by John Kindervag, a principal analyst at Forrester Research Inc. way back in 2010.
Now, in present times, with the increase of data volumes and soposticated cyber-attacks, the pressure of implementing Zero Trust as the technologies is gaining momentum.
Zero trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network, regardless sitting inside or outside of the network perimeter. It is a holistic approach for network security that incorporates several different principles and technologies.
Traditional IT network security, it is difficult to gain access from outside the network, whereas everyone inside the network is trusted by default. In effect, once an attacker gains access to the network, they have free reign over everything inside.
However, with present trends, enterprises no longer have their data in just one place; rather it is often spread across cloud. This makes the situation more difficult to have a single security control for an entire network.
Zero trust security means that no one is trusted by default from inside or outside the network and verification is required from everyone trying to gain access to resources on the network. With the rise of attack sophistication and insider threats, new security measures need to be adopted in order to restrict them from spreading once inside. Traditional security models were meant to protect the perimeter, threats that get inside the network are left invisible, uninspected and free to morph and move wherever they choose to successfully extract sensitive, valuable business data.
Zero Trust, rooted in the principle of “never trust, always verify,” is designed to address lateral threat movement within the network by leveraging micro-segmentation and granular perimeters enforcement, based on user, data and location. Lateral movement defines different techniques that attackers use to move through a network in search of valuable assets and data. With traditional perimeter-based security, businesses can define sub-perimeters within their organization networks using a specific set of rules for each using context around user, application traffic direction, etc. These sub-perimeters are designed to identify the spread of an attack within an organization and stop the unrestricted lateral movement throughout the network.
Core Principles and Technologies
Zero Trust works on the principle that nothing should be trusted and should always be verified. Within this framework, several technologies and best practices make up a Zero Trust architecture. Here are a few of the main principles:
- No Trust, a philosophy behind a zero trust network assumes that there are attackers both within and outside of the network and in effect, no one should be automatically trusted.
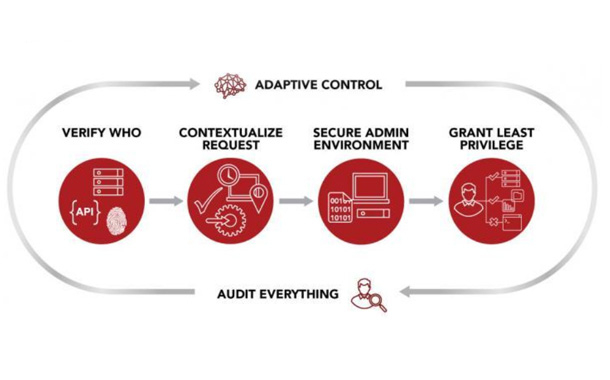
- Least-privilege access, which means only allowing access to the information someone needs. This reduces pathways typically used by malware and attackers and reduces the chances of internal data exfiltration.
- Micro-segmentation divides a network into separate segments with different access credentials. This increases the means of protection and keeps bad actors from running rampant through the network even if one segment is breached.
- Multi-Factor Authentication (MFA) requires two or more ways to prove someone is who they say they are. Using an MFA tool provides reliable identity verification that is necessary for any Zero Trust model. MFA simply means requiring more than one piece of evidence to authenticate a user; just entering a password is not enough to gain access.
- Risk-adaptive security controls are necessary in order to analyze human and entity behavior and identify potentially risky activities in near-real time. Gartner calls this Continuous Adaptive Risk and Trust Assessment (CARTA).
- Access Control: In addition to controls on user access, zero trust also requires strict controls on device access. Zero trust systems need to monitor how many different devices are trying to access their network and ensure that every device is authorized. This further minimizes the attack surface of the network.
The Objective
- Data Protection: Ensuring all data and resources are accessed securely, based on user and location. The traffic and data flow need to be identified so that it can map the business flows, and in order to have the visibility to the application, users and flows. Understanding who the users are, what applications they are using and the appropriate connection method is the only way to determine and enforce policy that ensures secure access to your data.
- Access Control: Adoption of a least-privileged access strategy and strictly enforce access control. By doing this, businesses can significantly reduce the pathways for attackers and malware.
- Introspection: Always all traffics are to be logged and inspected. Effectiveness of the same lies in identification of the appropriate junctions for inspection and build in the inspection points. Security rules, based on business policies, should be used to identify and allow or deny the traffic and activity to move through the “inspection points” gating your sub perimeters. This enables the segmentation of sensitive resources and establishes trust boundaries to help prevent the exfiltration of sensitive data.
- More authentication methods to add to counter credential based attacks.
- Never trust, always keep adding context and keep your roles up-to-date.
The Model:
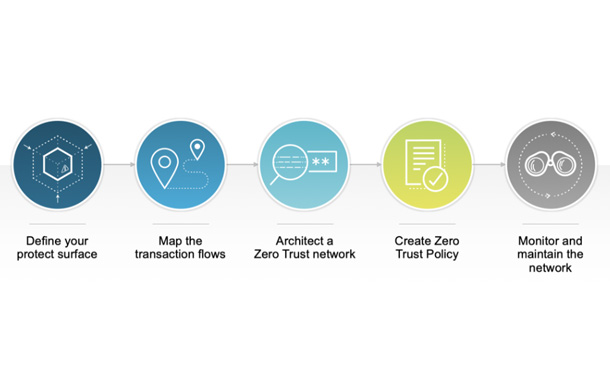
Forrester has outlined a roadmap for a successful zero trust implementation. Here is Forrester’s five-step model, paraphrased:
- Identify your sensitive data at rest and in motion
- Perform data discovery and classification
- Segment and zone the network based on data classification
- Map the acceptable routes for sensitive data access and egress
- Classify all resources involved in the electronic exchange of sensitive data
- Evaluate the workflow of data and redesign, if necessary
- Verify the existing workflows, like PCI architectures, and verify designs
- Architect zero trust micro perimeters
- Define micro perimeters, zones, and segmentation around sensitive data
- Enforce segmentation using physical and virtual security controls
- Establish access based on these controls and the micro perimeter designs
- Automate rule and access policy baselines
- Audit and log all access and change control
- Monitor the zero trust environment, in detail, with security analytics
- Leverage and identify existing security analytics solutions already existing within the organization
- Determine the logical architecture and best placement for your security analytics tools
- If a new solution is needed, identify a vendor that is moving in the same security direction as your organization and that can provide analytics for your other security solutions
- Embrace security automation and adaptive response
- Translate business process into technology automation
- Document, assess, and test security operation center policies and procedures for effectiveness and response
- Correlate policies and procedures with security analytics automation and determine what can be lifted from manual processes.
- Verify the security and implementation of automation within your environment and current solutions
Implementation Roadmap
There can be multiple approaches to the model but there are a few considerations most everyone will need to include in order to implement an efficient Zero Trust architecture:
- Consider the technologies you will need to add to your current stack such as:
- Next Generation Firewall
- Risk-Adaptive Security Tools
- Multi-Factor Authentication
- Secure Web and Email Gateways
- Threat Isolation and Network Sandboxing
- Network Forensics and Encrypted Traffic Management
- Privileged Access Management or Identity Management
- Vulnerability Management
- Security information and event management along with Security Orchestration and Automation
- Data Loss Prevention (DLP) and User Behavior Analysis (UBA)
- Cloud Application Security
- Adopt Zero Trust Security Best Practices
- Add prioritized cloud technologies to replace unauthenticated legacy services and systems.
- Design zero trust architecture based on how data moves across the network, and how users and apps access sensitive information.
- Extend identity controls to the endpoint to recognize and validate all devices. Just verifying users is not enough.
- Organize users by group/role to support device policies. For more insight on implementing Privileged Identity Management (PIM), read our article here.
- Leverage automatic de-provisioning, along with the capacity to wipe, lock and un-enroll stolen or lost devices.
- Educate and coach end users to be part of the solution in the new zero trust environment. Otherwise, they will be part of the problem.
- Regularly update end user rights based on changes to roles/jobs, as well as changes to prevailing security policies and compliance requirements.
- Understand Access Needs – decide who needs access to what in your organization. Remember to grant the least privilege that someone needs and nothing extra.
- Consider Your Culture – at the macro level and at the granular security level a company’s culture will dictate the efficacy of any security model. In the case of Zero Trust where you understand the threats come from outside and within, a supportive and educated workforce is key.
Authored By: Sushobhan Mukherjee, Chairman- Infosec Foundation& Co-founder and CEO of Prime Infoserv LLP


