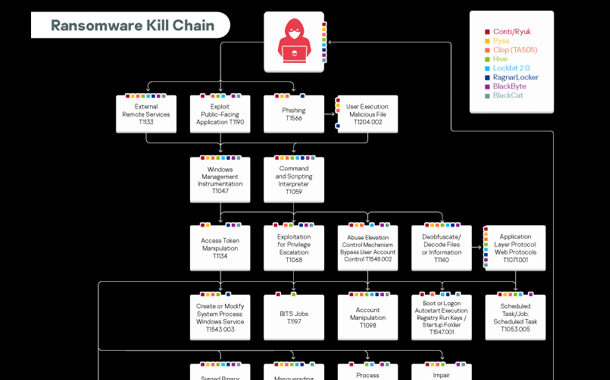
Kaspersky’s Threat intelligence team has conducted analysis into the most common tactics, techniques, and procedures (TTPs) used by 8 most prolific ransomware groups such as Conti and Lockbit2.0 during their attacks. The research revealed that different groups share more than half of the cyber kill chain and execute the core stages of an attack identically. This monumental study of modern ransomware, which is available for free, will serve as an aid in understanding how ransomware groups operate and how to defend against their attacks.
The analysis within the guide focuses on the activity of Conti/Ryuk, Pysa, Clop (TA505), Hive, Lockbit2.0, RagnarLocker, BlackByte and BlackCat. These groups have been active in the United States, Great Britain and Germany, and have targeted over 500 organizations within industries such as manufacturing, software development and small business, between March, 2021 and March, 2022.
The 150-page guide navigates readers through the stages of ransomware deployment, how cybercriminals use their preferred tools and the goals they are hoping to achieve. Readers can also learn how to defend against targeted ransomware attacks and learn about SIGMA detection rules, which can be used to build up their preventive measures against the attackers.
Kaspersky’s Threat intelligence team analyzed how the ransomware groups employed the techniques and tactics described in MITRE ATT&CK and found a lot of similarities among their TTPs throughout the cyber kill chain. The revealed ways the groups attacked proved to be quite predictable, with ransomware attacks following a pattern that includes the corporate network or victim’s computer, delivering malware, further discovery, credential access, deleting shadow copies, removing backups and, finally, achieving their objectives.
The researchers also explain where the similarity between attacks comes from. The emergence of a phenomenon called ‘Ransomware-as-a-Service’ (RaaS), where the ransomware groups do not deliver malware by themselves, but only provide the data encryption services. Since the people who deliver malicious files also want to simplify their lives, they use template delivery methods or automation tools to gain access. Also, reusing old and similar tools makes life easier for attackers and reduces the time it takes to prepare an attack. Reusing common TTPs have also made hacking easier. Although it is possible to detect such techniques, it’s much harder to do preventively across all possible threat vectors. Besides, slow installation of updates and patches among victims is a reality. It is often the case that those who are vulnerable are attacked. The systematization of various TTPs used by attackers has led to the formation of a general set of SIGMA rules in accordance with MITRE ATT&CK – which helps to prevent such attacks.
Nikita Nazarov, Team Lead Threat Intelligence Group at Kaspersky, says, “In the past few years, ransomware has become a nightmare for the whole cybersecurity industry, with constant developments and improvements being made by ransomware operators. It is time consuming and often challenging for cybersecurity specialists to study every single ransomware group and follow each one’s activities and developments, in a bid to win the race between attackers and defenders. We have been tracking the activity of various ransomware groups for a long time, and this report represents the results of a huge piece of analytical work. Its purpose is to serve as a guide for cybersecurity professionals working in all kinds of organizations, making their jobs easie.”
This report is aimed at SOC analysts, threat hunting teams, cyberthreat intelligence analysts, digital forensics specialists and cybersecurity specialists involved in the incident response process and/or those who want to protect the environment they are responsible for from targeted ransomware attacks.
Kaspersky has laid down certain rules to help users protect themselves and their businesses from ransomware attacks. For the benefit of our readers, we are putting them together below:
- Do not expose remote desktop services (such as RDP) to public networks unless absolutely necessary and always use strong passwords for them.
- Promptly install available patches for commercial VPN solutions providing access for remote employees and acting as gateways in your network.
- Always keep software updated on all the devices you use to prevent ransomware from exploiting vulnerabilities
- Focus your defense strategy on detecting lateral movements and data exfiltration to the Internet. Pay special attention to the outgoing traffic to detect cybercriminals’ connections.
- Back up data regularly. Make sure you can quickly access it in an emergency when needed.
- Use solutions like Kaspersky Endpoint Detection and Response Expert and Kaspersky Managed Detection and Response service which help to identify and stop the attack on early stages, before attackers reach their final goals.
- To protect the corporate environment, educate your employees. Dedicated training courses can help, such as the ones provided in the Kaspersky Automated Security Awareness Platform.
- Use a reliable endpoint security solution, such as Kaspersky Endpoint Security for Business that is powered by exploit prevention, behavior detection and a remediation engine that is able to roll back malicious actions. KESB also has self-defense mechanisms which can prevent its removal by cybercriminals.
- Use the latest Threat Intelligence information to stay aware of actual TTPs used by threat actors.
A single point of access for Kaspersky’s TI, the Kaspersky Threat Intelligence Portal provides cyberattack data and insights gathered by its team for over a period of 25 years. To help businesses enable effective defenses in these turbulent times, Kaspersky has announced access to independent, continuously updated and globally sourced information on ongoing cyberattacks and threats, at no charge.