With recent concerns around security and remote video conferencing, you may be asking – is my data secure? Is it encrypted? Security is one of our highest priorities and we understand it is yours too. Your data is protected with a multi-layered and faceted approach to security and privacy while still enabling many of the GoToMeeting features our customers have grown to love and expect.
How Data is Secured While Transmitted
GoToMeeting offers our customers the ability to remotely communicate and interact with each other, share desktop content and chat with meeting attendees. However, for all of these features to work, data needs to be sent back and forth over public networks. It’s this exchange of information that makes it critical to ensure the right security controls and encryption mechanisms are in place to protect your meeting content.
Depending on the type of data and the client you use to join a remote meeting, different transport technologies can be used. Data must be secured while transmitted over the Internet – meaning encryption standards should be standardized, not vulnerable to known attacks, and encryption keys must be exchanged in a secure way. Below are the types of transport technologies meeting content can be exchanged with.
- Secure Real-Time Transport Protocol (SRTP) and HTTPS – provides encryption, message authentication and data integrity.
- The Multicast Protocol – a custom protocol that provides optimized bandwidth quality and uses Transport Layer Security (TLS) for transport encryption and additionally provides an overlay encryption using AES (Advanced Encryption Standard) in Counter Mode (CTR mode).
- Audio/Video Transport Protocol (AVTP), a custom protocol optimizing bandwidth that provides transport security similar to IPSec using AES in CTR mode. Keys are exchanged leveraging a previously established TLS connection.
End-to-End Encryption (E2EE) is a system of communication where only the communicating users can read the messages. While E2EE can provide desirable security properties, it also conflicts with some product features of remote collaboration tools. This reinforces the importance of a layered security approach.
Our Transport Technologies and Encryption Mechanisms
During an online meeting, GoToMeeting connects to different servers to send and receive meeting content. Independently of whether you join a GoToMeeting via Windows, MacOS, Android, iOS or the web client, your meeting content will be encrypted in transit between your client and our LogMeIn infrastructure with Advanced Encryption Standard (AES) with a key length of 128 bits in CTR mode at a minimum. You can find the details of these exchanges below:
- Our GoToMeeting clients use HTTPS to connect to our Web Services.
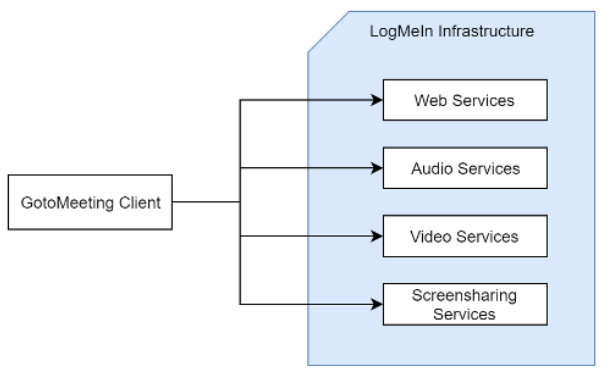
- To connect to the Audio and Video Services, the GoToMeeting Windows, MacOS, Android, iOS clients use the AVTP protocol that uses AES encryption in Counter Mode. Encryption keys are exchanged with a previously established TLS connection. The GoToMeeting web client uses SRTP with AES encryption.
- Connections to the Screensharing Services and meeting chat rooms sit on top of TLS and uses an additional overlay encryption by AES.
When an organizer records a meeting, that data is stored in AWS S3 using proper access controls and server-side encryption and organizers can control the sharing of that content. It is important to note that meeting content is never recorded unless the organizer explicitly starts a recording. Additionally, we provide account admins with the option to deactivate the cloud-based recording feature for all users in their account if they choose to do so.
To provide you with a seamless experience when connecting remotely with friends and family, we strive to offer unparalleled optimization and bandwidth. For example: to dial into a meeting with a PSTN based phone (a wired phone system over which landlines calls are made) and to mix audio into a single stream, we need to decrypt the audio, or to scale videos so attendees can view each other’s webcam, we decrypt video data within our infrastructure. Organizers can also choose to deactivate this type of dial-in if they don’t want their meeting data to be sent over the publicly switched phone network.
If you’re a GoToMeeting account admin, you are given the control and flexibility to turn features on and off that work for you and your organization. Admins can learn more about the new GoToMeeting here.
Documenting our stringent internal security controls and mechanisms, we hold several third-party security certifications such as the SOC2, SOC3, and BSI C5 to provide transparency of our security controls. You can read more about LogMeIn’s Stance on Security and Privacy here as well as on our Trust and Privacy Center.
The key to successful, secure virtual meetings is to be aware of and practice proper security measures while remote working. As a meeting organizer, you can also take advantage of the innovative features like meeting locks and password protection GoToMeeting offers to protect you and your participants’ information. Check out our 5 best practices to staying secure on GoToMeeting.



